Secret inputs for models
We’ve added a way to securely pass sensitive values to models.
In Cog v0.9.7 and later,
you can annotate an input with the Secret type
to signify that an input holds sensitive information,
like a password or API token.
from cog import BasePredictor, Secret
class Predictor(BasePredictor):
def predict(self, api_token: Secret) -> None:
# Prints '**********'
print(api_token)
# Use get_secret_value method to see the secret's content.
print(api_token.get_secret_value())Replicate treats secret inputs differently throughout its system.
When you create a prediction on Replicate,
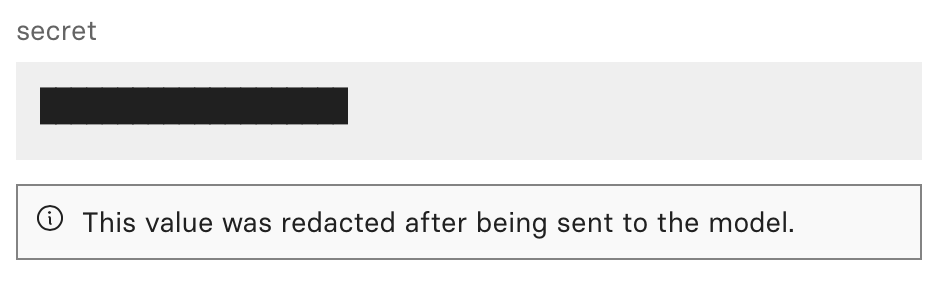
any value passed to a Secret input is redacted after being sent to the model.
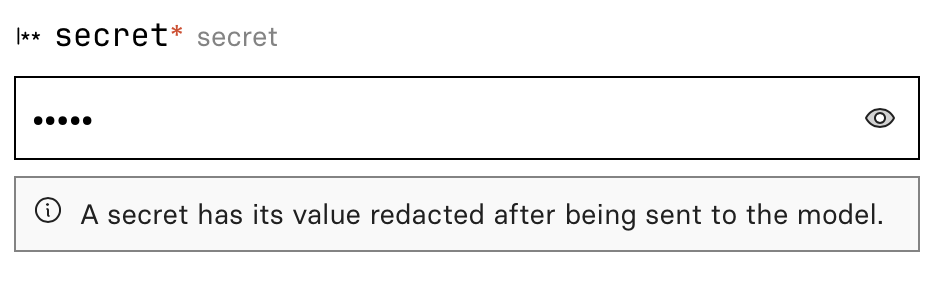
Before
After
Caution: Passing secret values to untrusted models can result in unintended disclosure, exfiltration, or misuse of sensitive data.